Products
_
_
_
_
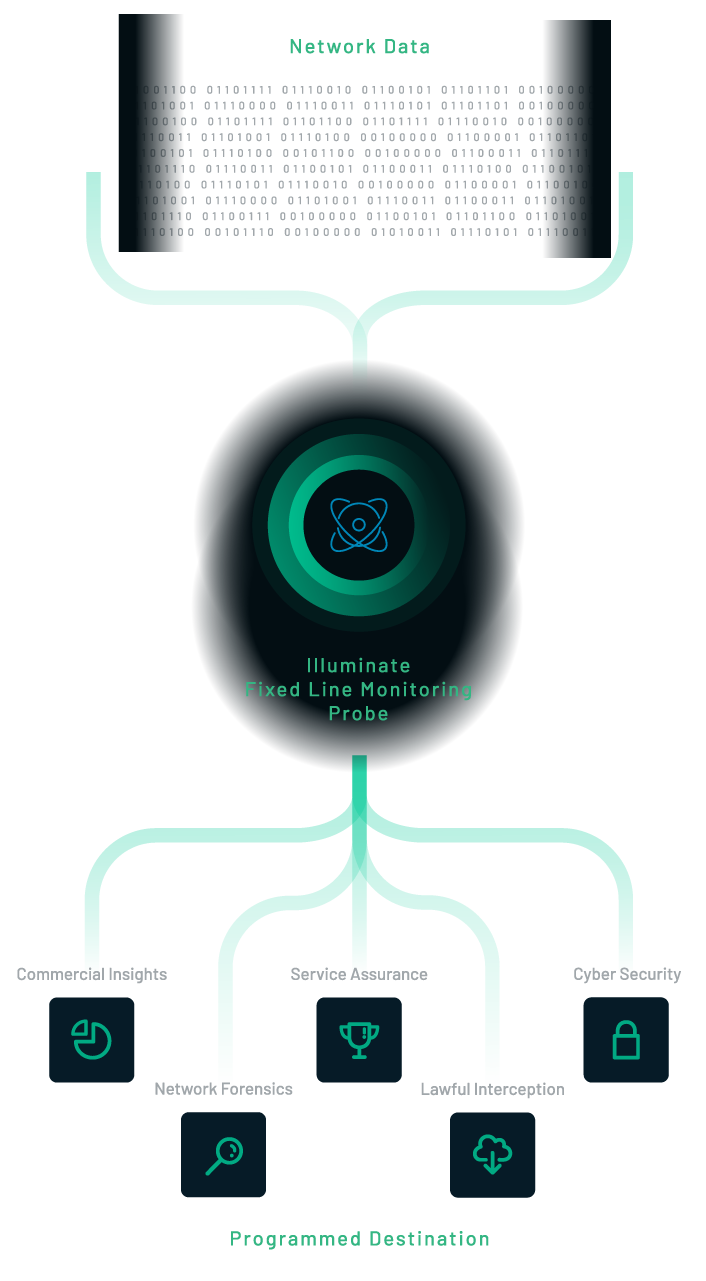
Fixed Line Monitoring
Capture and analyze traffic on any network, whether that is specific, intelligence-driven streams of data or full take metadata and content, our products and solutions scale to meet your needs.